Martian Encryption App VCL & Standard Martian Text Encryptor
The applications are provided as freeware without warranty of any kind, for users to use at their own risk with a good conscience.
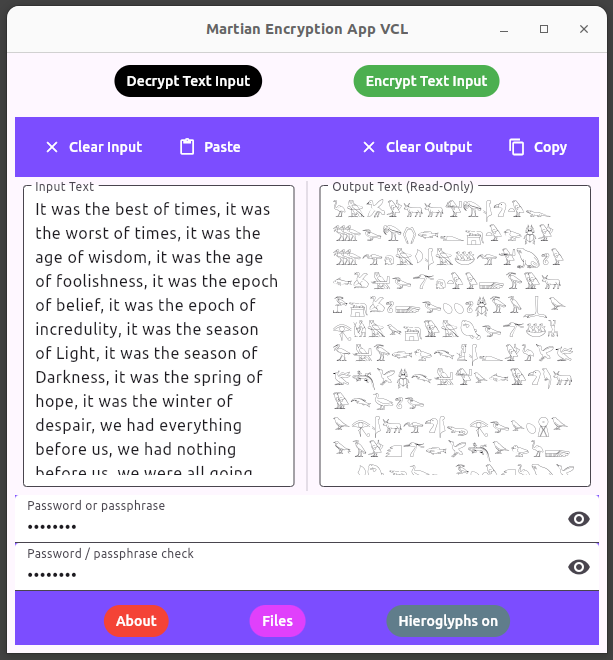
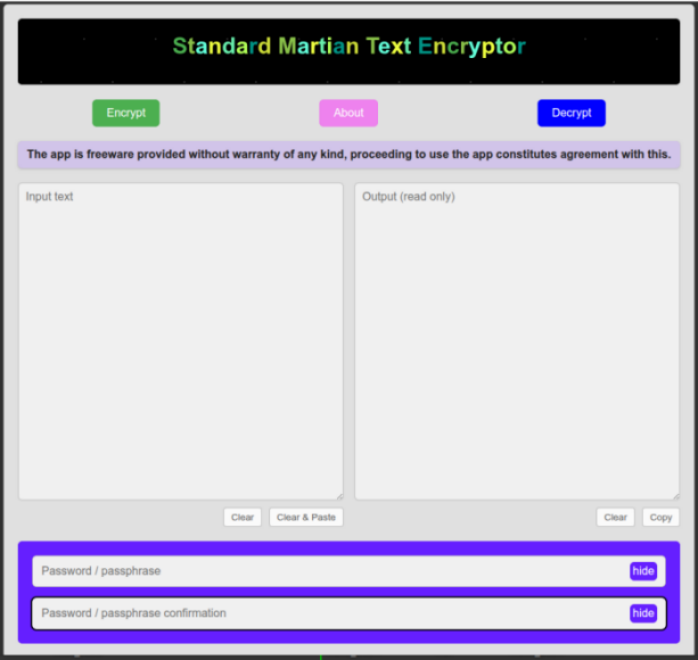
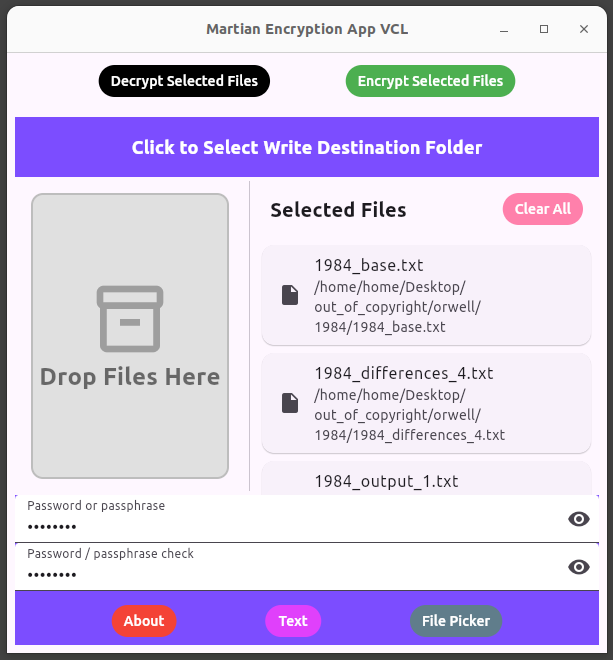
The Martian Encryption System comprises of a desktop application, Martian Encryption App VCL, and a single page web application variant, Standard Martian Text Encryptor.
Martian Encryption App VCL has been tested on Ubuntu 22.04 / 24.04 and Windows 10, it encrypts and decrypts both input text and files. The lighter weight web page variant, Standard Martian Text Encryptor works only with text inputs. Both the web and desktop applications will decrypt each other's encrypted text should the password be correct.
An artisan project, testing has only been conducted by the developer, there has been no external audit of the code or the system. Besides the creative rationale to make the system, there is a case that the workload of those who seek to defeat encryption systems is added to, the more of them there are.
If using the Standard Martian Text Encryptor, the recommendation is to save the web page to your device, and use that. The principle benefit of this is that 'you have the application' should it be withdrawn or support for it cease for whatever reason. IMPORTANT: should you save the application as a webpage, ensure all input and output fields are blank or the data in them will also be saved!
At time of writing (summer 2025) the case for encryption in the UK, is increasingly strong in view of the legislative framework and the way certain laws can be used. For example, the UK government can compel a service provider to allow access to a user's private data stored on their servers, a service provider obliged to decrypt the data if it is encrypted by them, this all done in absolute secrecy without even the fact of the order allowed to be disclosed. The Martian system 'defeats this' as the user encrypts their own data, and therefore providing the password used is sufficiently unpredictable, no one else can decrypt it. This means, an individual should be made aware of surveillance as an order to provide unencrypted access to their data, can only be made directly to them. An improvement on a situation where an individual might have no idea their communication is being decrypted and monitored by the state.
The web application with a little paradox ..., does not require an internet connection to work. Once the page has been loaded, everything to encrypt and decrypt text exists in a format known as a 'single page web application' on the user's device. Thus the webpage can be saved to device for offline use, and is fully functional when a web browser is used to load it as an offline web page. Online or offline, all processing takes place on the user's device. Neither the web application nor the desktop application connect to the internet themselves. Both are designed as privacy tools, the developer does not use them to collect user data and encourages for peace of mind, disconnecting a device from the internet when using these tools.
Web browser tools enable an inspection of the web page variant code in full. The encryption system is built on the premise whereby it is assumed knowledge of the encryption code is in the hands of any adversary. A user's defense is a secret and unpredictable password.
Encryption of both files and text is by way of two streams of cipher data, the streams seeded and built using the user's encryption password. Each encryption will use a different stream even with the same user password, as the seed also involves an 'assume public knowledge random modifier' with a length of 64 characters, the user password is combined with this to ensure cipherstreams never repeat. The assumption of public knowledge regarding the modifier, is because without knowledge of it, decryption cannot take place. The modifier is included in encrypted outputs in an obscured unencrypted form, but by itself without the user password is useless.
The encryption process takes a split of one of the cipherstreams to select a substitution table, to swap an unencrypted byte for the byte value occupying its position in the table. The other cipherstream is then used to perform an operation known as XORing, whereby the byte is transformed according to the byte it is XORed with, remember it has already been swapped at this point. The XORed byte is then swapped with a byte in another table, decided by the other half of the previously split cipherstream. In something like 1 case in 16 the same table will be used for both substitution table swaps. Although a byte is only transformed from a value of 0 to 255 to another value of 0 to 255, the number of possible routes it might take is in the thousands. This is the basis of the Martian Encryption System. Decryption is reversing these steps using the same cipherstreams seeded by the user password combined with the per encryption modifier.
The apps are provided without warranty of any kind, always check you can decrypt what you encrypt before deleting any source material.
An encryption is only as strong as a password or passphrase is unpredictable and secure with a system like this.
The system is not designed to be the fastest, but to involve significant computational penalty to impair brute force cracking attempts. To test a password in a cracking attempt, a significant amount of computational work needs to be done beforehand making the initial cipherstreams. The clever ruse of reversing the cipherstreams before they are used, means a hacking attempt needs to go to the length of building the entire first load of cipher, to test a password on the first few bytes of encrypted text or file. The trade off with this hardened design means a 'low end' device might take 90 seconds or longer to derive the cipherstream to encrypt or decrypt, both a novel length piece of text or a single sentence. The length of the material is secondary to the computational work involved making the cipher. The likelihood is the application is not broken if it appears to hang on a 'please wait' screen on a budget smartphone, it is busy building the cipherstream.
Note, there is no password or passphrase recovery with this system, it is designed for ease of use by careful users who are encouraged to experiment to familiarize themselves with the applications. Passwords / passphrases are left in place after app actions, for convenience. The default setting for obscuring passwords / passphrases is off, again for convenience.
With the desktop application, with files, select a write directory for the app to write to. Drag files to be encrypted or decrypted into the drop zone, or use the file picker. When encryption or decryption is underway, do not add, delete or open files in the write directory in case it causes a conflict with those being processed. Files the app writes are not ready for use until a process finishes, although they will appear in the write directory when a process starts, they are not fully written until it concludes. For encryption a check on the password or passphrase needs to match. Encrypted files the app writes can be identified by the .martian extension appended to their name.
The desktop app will only attempt to decrypt files with the .martian extension appended to their name, writing the file with the extension lopped off if no file with that name exists in the write directory. On decryption, if you get the password wrong, with files a file is still written, but it will be garbage data. To keep the app within its design brief, it does not itself delete these garbage files. A report at the end of decryption will detail successes and fails.
The user can themselves rename files to remove the .martian extension, but it must be added back for the decryptor to identify it as a file it can decrypt.
With the selected file list, you can use the button to clear all files, or click on an individual file to remove it from the file list.
With both the desktop and web apps, text block encryption accepts inputs of varying length but generally up to the millions of characters realm. With the desktop app, the 'hieroglyphs' toggle button does not really encrypt using hieroglyphs, rather substitutes hieroglyph characters as the output font when encrypting only. When these hieroglyphs might be copy pasted from the app, they will display as ordinary (although encrypted and encoded to base64) characters according to an application font. Note, this type of input is easily corrupted by invisible formatting information outside of the context of plain text that might be used by word processors, etcetera.
The web application does not feature the hieroglyphs font, only the desktop app.
The apps are provided without warranty of any kind. The onus is on the user to ensure they can decrypt what they encrypt using them. The onus is also on the user to retain the software and a machine to run it on in case it might be withdrawn. With caveats, nothing else will decrypt what these apps encrypt.
And a final note on browser security prompts when using the copy button on the web application, the prompt does not apply to the fact "Smartphone Projects" is not requesting a copy of your data, it is a more generally worded broswer alert. The code triggering the copy request, is in the web application running in your browser, but where you paste anything is at your discretion. The single page web application is neither maintaining nor coded to trigger a web connection, the code can be inspected using browser developer tools.
- Visit the webpage where the Standard Martian Text Encryptor single page web application resides to use the text encryptor / decryptor, or save the webpage to your device, or inspect the code. If the webpage is saved on a USB flash drive, it can be launched from there.
- Download a zip and run Martian Encryption App VCL version 1.0.0 (martian_ea_vcl_1.0.0_win.exe) after unzipping on Windows from a folder, tested on Windows 10. This method allows the application to be stored on and launched from a USB flash drive.
- Download a tar.gz and run the Martian Encryption App VCL version 1.0.0 executable (martian_ea_vcl_1.0.0_lin) from its folder after unzipping on Linux, tested on Ubuntu 22.04 & 24.04. This method allows the application to be stored on and launched from a USB flash drive.
Windows users are advised that Smartphone Projects Ltd is not an approved by Microsoft software vendor and they may need to override warnings to run the software on their system.