Project govnolike
The app is provided as freeware without warranty of any kind, for users to use at their own risk with a good conscience.
The latest version of the app that supersedes all prior versions is 2.2.0. This will decrypt output from earlier versions, but earlier versions will not decrypt output from later versions. Slower than the previous version, the latest version imposes a "serious computational penalty" generating the encryption key as an obstacle to brute force attacks and is thus vastly superior to its predecessor.
Note, this application is not designed for slap dash use. It is a serious privacy tool, users are advised to "get the hang of it" by way of some experimentation before relying on it. Clicking / tapping the "About Important" button when the app launches is vital for a more comprehensive understanding of various issues. Smartphone Projects Ltd does not enter into correspondence in regard to this freeware, the onus is on the user to ensure they can decrypt what they encrypt by way of their own practice.
In February 2025 press reports suggested that the Government of the United Kingdom had requested
decrypted file access, to user files stored encrypted by a major technology company. This provided the initial impetus to make this app,
with the notion that "the government won't like this" transmogrified into "govnolike" - the name of the app.
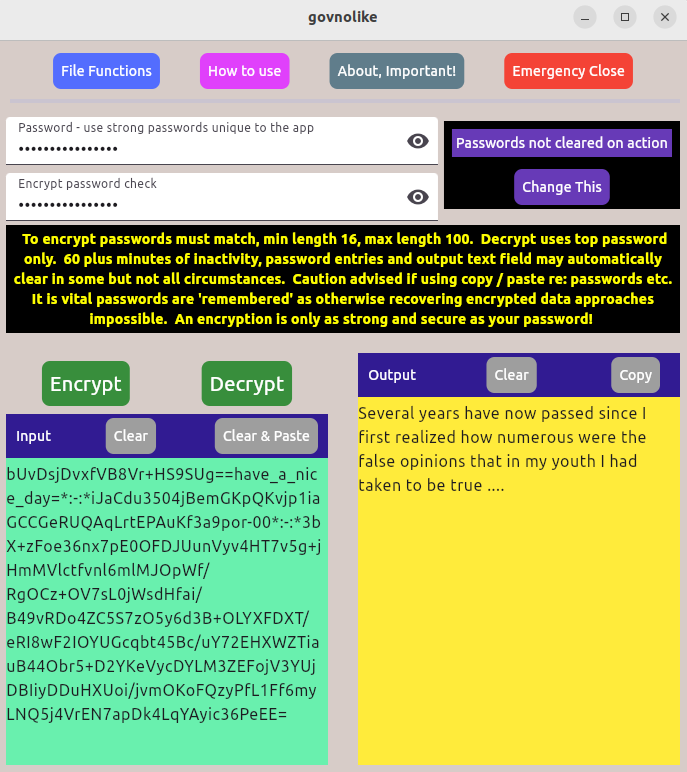
Govnolike is free light weight text and file encryption application, tested on Windows 10™ and Ubuntu Linux® distributions 22.04
and 24.04. The application uses the AES-256 algorithm to encrypt user text and files, the encryption key derived
from a minimum 16 character user password combined with a substantial modifier, SHA-256 hashed.
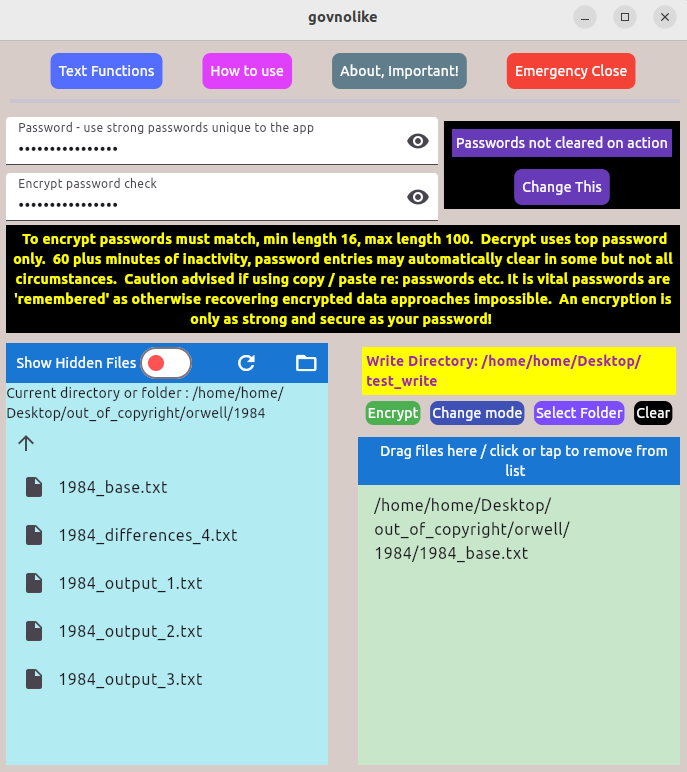
The application does not delete or modify user files, it produces new encrypted and decrypted files based on what is input -
the onus is on the user to satisfy themselves that an encryption can be decrypted before deleting any
source material themselves. The onus is also on the user to keep a copy of the govnolike application, and a machine that will run it -
this, as there is no guarantee that new versions of the software will be produced to run on later operating systems,
or that Smartphone Projects will continue to distribute it.
The strength of the system relies on the unpredictability and security of the password used for
encryption, it is very important to appreciate this, and how password cracking is based on known passwords
and predictable patterns that passwords are often made from.
The app itself has no online
connectivity, and can be used on an offline machine. There is no password recovery with it, and thus
retaining a reference to a password used to encrypt is
vital in order to decrypt.
The idea behind text block encryption is for communication between parties to be secured, by
their shared knowledge of the
encryption password, encrypted text copy pasted into email for example, very importantly it remaining in an encrypted plain text format without the addition of any
invisible to the eye formatting information. Whilst this type of thing might
be vulnerable to leaks and spies, keystroke loggers and
screen recorders, it is for example, an improvement on unencrypted text being evident in a sent or received communication.
Users are advised they may be obliged to decrypt what they encrypt using the app by legal order.
In regard to this, as the user encrypts themselves and it is not done for them by an online service also providing storage, the situation should not arise whereby the user is
oblivious to their encrypted data being decrypted by the service provider under an obligation to do so without informing the user.
Note, if a password is not sufficiently unpredictable, then an attacker with the resource to make a substantial number of guesses per second
might not take a great deal of time to arrive at even a 16 character password.
It is important that encrypted output remains exactly as initially outputted in order to be decrypted. Bear in mind things
like word processors and email clients may well adulterate encrypted material inserting invisible formatting information, etcetera. Providing
encrypted text remains in plain text format, it should decrypt as it will be exactly as outputted. The same applies to encrypted files,
they cannot be modified or decryption will fail. Test what you encrypt can be decrypted in line with your use cases.
A reminder, the security of the system relies on the unpredictability and secrecy of a user password, user retention of any passwords,
and the user having access to the application and a machine that will run it. The app is provided without
warranty of any kind, for users to use at their own risk with a good conscience.
- Download the Windows™ installer for version 2.2.0, tested on Windows 10.
- Download a zip and run the govnolike executable version 2.2.0 from its folder after unzipping on Windows, tested on Windows 10.
- Download a tar.gz and run the govnolike 2.2.0 executable from its folder after unzipping on Linux, tested on Ubuntu 22.04 & 22.04.
Windows users are advised that Smartphone Projects Ltd is not an approved by Microsoft software vendor and they will need to override warnings to run / install the software. The app design adheres to the principle whereby public knowledge of the exact encryption methodology it is irrelevant providing the key used remains secret and is unpredictable.